In digital marketing, speed and trust are critical to success. Agencies that activate quickly get results, and today's teams are employing scalable SaaS tools such as CRM systems and project management platforms. Automation is necessary to activate results fast.
SaaS platforms come with a significant responsibility regarding data security risks. A data breach, poorly managed access, or an unintentional mistake could make for an expensive fix. Even worse, it harms the trust you've built with your clients and threatens the agency’s brand. In fact, organizations are investing more in SaaS security because it is perceived as necessary for long-term viability rather than an expense.
A proactive, step-by-step approach to SaaS platform security will make a considerable difference for agency owners and operations managers. What could often feel like compliance is actually supporting your team’s ability to increase efficiency and effectiveness in the agency world.
Here is a framework to help your team feel secure with your SaaS ecosystem and continue running the agency effectively.
Step 1: Secure the Gate with IAM (Identity and Access Management)
The greatest point of failure in any SaaS setting is unauthorized access, largely driven by compromised credentials. IAM (Identity & Access Management) is the foundational aspect of how access is granted and to which resources.
Require Multi-Factor Authentication (MFA) Everywhere
You must mandate Multi-Factor Authentication (MFA) for all administrative, client-facing, and other sensitive applications. MFA requires two or more verification factors from users to access an application, reducing the likelihood of compromised accounts even if passwords are stolen through phishing or trust-based social engineering attacks.

Image Source: Secret Double Octopus
Pro Tip: Don't treat MFA as a once-and-done exercise. Audit your MFA flows at least once a year to verify they continue to function as intended. Treat this as a necessary administrative task.
Adopt Single Sign-On (SSO)
Single Sign-On (SSO) improves agency productivity. SSO essentially enables users to access multiple applications with a single set of credentials.
- Unified Security: SSO provides centralized control over who can access which systems.
- Reduced Friction: SSO reduces password fatigue for clients and employees alike, increases job satisfaction, and enhances productivity.
- Improved Defense: When paired with MFA, SSO continues to maintain this layered defense regarding login access, without burdening the user with initial login efficiency.
Use SSO systems, such as Scalefusion OneIdP, Okta or Azure AD, to centralize authentication for all staff and third-party partners.
Implement Least Privilege Access (LPA)
The principle of least privilege (LPA) requires that users, applications, and processes be granted only the minimum permissions necessary to execute their tasks—and nothing more. This principle prohibits lateral movement in the event of an account being compromised!
Agencies should consider role-based access control (RBAC). These permissions can be defined by agency roles (e.g., Marketing Specialist vs. Account Manager). You can use role assignments in your Project Management Software or CRM to minimize access to excessive privileges.
Conduct privilege audits to eliminate access levels for accounts that have accumulated excessive access privileges beyond their intended scope over time.
Step 2: Achieve Total Visibility of Your SaaS Stack
The scalability of cloud solutions often leads to a proliferation of applications. When employees leverage solutions on their own without going through IT, it creates what's known as Shadow IT. Their invisibility is one of the most significant security risks and creates gaps in your compliance and risk mitigation.
Keep an Exhaustive Inventory of Applications
If you can't see it, you can't secure it. Marketing teams frequently adopt freemium tools or departmental SaaS without regard to procurement, creating unauthorized data paths that may also bypass security controls.
Introduce continuous application discovery tools that can inventory all applications sanctioned for access to company data in the enterprise and all (Shadow IT or unsanctioned) applications that can access company data in the enterprise.
Use SaaS Security Posture Management (SSPM)
SSPM is the central management tool for understanding the security settings of all of your sanctioned apps (e.g., your enhanced CRM software, InstaSites, etc). It is a purpose-built toolset for understanding misconfiguration, managing permissioning, and driving compliance across your SaaS tool stack.
- Misconfiguration Discovery: Incorrectly configured settings, whether public sharing of sensitive data, relaxed sharing, or even turned off MFA, are a leading cause of breaches. SSPM continuously monitors configuration status and compares it to a set of standards. It can notify you immediately of any deviation.
- Centralized Monitoring: SSPM produces a singular dashboard for reviewing security posture, allowing security teams to measure performance over time and monitor remediations undertaken by developers and other personnel.
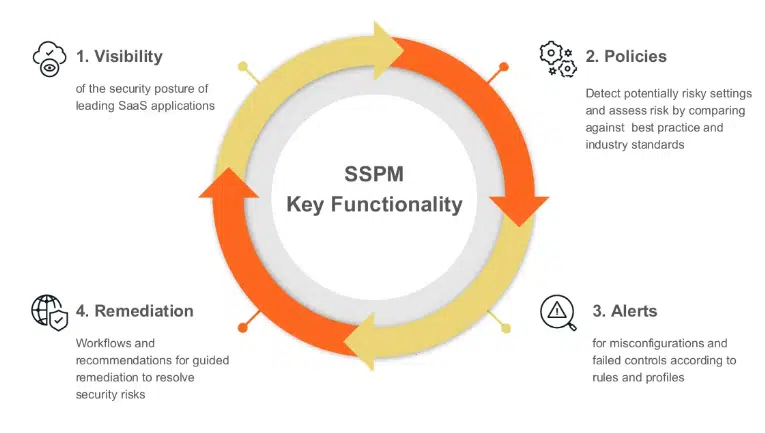
Image Source: CybeReady
Use SSPM to monitor applications with high-risk profiles continuously to detect any security risks or compliance gaps (e.g., validate the configuration meets HIPAA or SOC 2 compliance).
Step 3: Securing Client Data with Encryption and Compliance
Securing the sensitive client data you oversee, whether in the campaign performance metrics provided by Social Media Reports or in the CRM databases, is foundational to establishing client loyalty.
Require Data Encryption
Encryption is at the core of protecting data in the cloud. Agencies must ensure that all sensitive data is encrypted:
- At Rest: Data at rest (in other words, stored data like in databases or cloud storage) must use strong standards of encryption, such as AES-256.
- In Transit: Data that is in transit (moving through your applications/systems, and client browsers) must use TLS encryption (HTTPS).
When you build a client’s website with an external platform, ensure that they are using SSL certificate and secure hosting so that you minimize fraud and data compromises.
Continuous Monitoring for Compliance
Employee and client trust, combined with scalability, comes from your compliance with applicable global standards (e.g., SOC 2, ISO, GDPR). If organizations fail to comply with these standards, they are subject to significant financial fines and can even be forced to stop operating pending an investigation.
Regularly monitor your SaaS configurations against predefined compliance frameworks. There are SaaS security solutions that can automate your compliance monitoring process, making your audit preparation much easier and reducing the expense and employee time spent redoing manual reviews.
Step 4: Securing Automation and Integrations
SaaS environments are built to improve operational efficiency through automation, whether it be driving sales pipelines or employing third-party integration to scale tasks. However, it is important to remember that these integrations rely on APIs (Application Programming Interfaces) to bridge across systems. If APIs are not designed securely, they can be attacked, serving as an entry point and exposing sensitive information.
The main goal of API security controls is to protect the endpoints that automate data exchanges.
- Authentication & Authorization: Use the industry standards of OAuth 2.0 type connectivity processes to ensure proper token usage. If third-party apps are hijacked, we certainly do not want malicious actors to have sustained access to multiple systems.
- Rate Limiting: To avoid Denial-of-Service (DoS) attacks, ensure there is some rate-limiting applied to API communication that will enable a user to send a flurry of communication to your system prior to being considered with another legitimate request.
- Input Validation: Sanitize and validate all input parameters to avoid injection attacks (SQL injection, some common terminology), sending malicious code through the API.
Implement integration approval workflows and an ongoing auditing process for third-party apps needing API/OAuth connectivity, to review the permissions requested and confirm they are narrow as a business function.
Step 5: Operationalize Security for Continuous Improvement
Security isn't a one-off project but an iterative process. You need to integrate continuous security improvements into your operational requirements and project management workflows.
Implement Continuous Monitoring and SIEM
One of the most significant steps in protecting your platform is instituting systems that continuously monitor user activities and identify non-conforming behavior.
- Detection: Leverage technologies that incorporate user behavior analytics that can identify when an account is acting strangely, such as multiple downloads of sensitive data or logins from locations that are not the norm.
- Logging: Introduce SIEM (Security Information and Event Management) solutions that combine and analyze security logs across every system that you implement, so that suspicious conduct can be identified.
- Response: Integrate SIEM with SOAR (Security Orchestration, Automation, and Response) features to help automate responses to threats (thus drastically reducing the time it takes to remediate incidents).
Be Prepared with Incident Response Planning (IRP)
When a breach occurs, it's about speed. Your agency needs a defined security Incident Response Plan (IRP) with allocations for action roles that will help manage the event.
The incident workflow consists of:
- Identification: Confirming that an incident has occurred and identifying the type of incident and level of severity.
- Containment: Isolating systems that are affected, to eliminate the potential for spread (i.e., disabling compromised accounts temporarily).
- Eradication: Defeating the root cause of the incident, such as malware or access by unauthorized individuals.
- Recovery: Restoring systems from clean backup environments and validating the entire environment.
- Post Incident Review: Reviewing the incident to learn and improve your security posture.
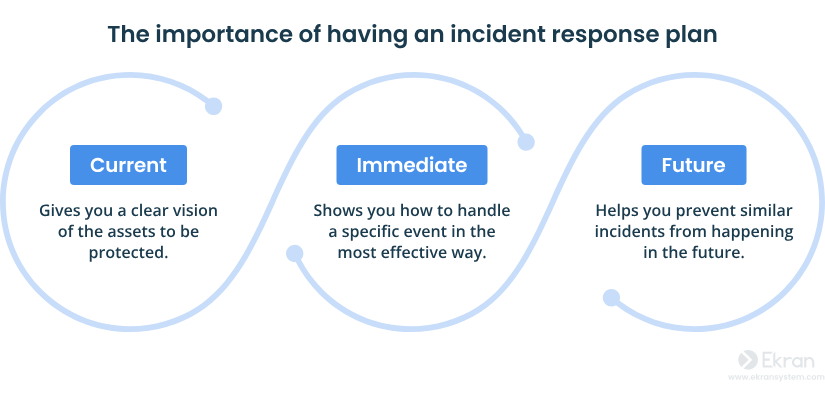
Image Source: Syteca
Champion Employee Training and Awareness
Human error remains one of the most common SaaS security risks available for attackers. Using phishing and social engineering techniques, attackers can easily exploit human errors. Even with excellent MFA implementation, it will be ineffective if employees are unaware of the latest tactics of threat actors.
Conduct regular training outlining the risks of Shadow IT and phishing. A well-informed team can be your best defense against all potential internal and external threats.
Conclusion
Protecting your SaaS platform does not mean restricting productivity; rather, it is about carefully optimizing operations and building resilience so that you can grow more, faster, and more securely. With the use of strong identity controls (MFA/SSO/LPA), centralized visibility through SSPM, and constant assessment of your automated environment, your organization reduces risk and enhances profitability.
Strong protections are your competitive advantage. Not only do they protect your clients' sensitive information, but they also maintain a compliance posture and allow you to position yourself as a trusted organization in the highly competitive space of digital marketing.


.svg)

.svg)
.svg)
.svg)
.svg)
.svg)
.svg)




.svg)
.svg)
.svg)
.svg)
.svg)